The protection of personal data and information is often the spotlight thanks to incidents like the Facebook and Cambridge Analytica scandal. But most information leaks are not due to companies willingly selling your data. Rather, they are the result of breaches and hacks.
To make matters worse, you often only hear about these data breaches years later. Luckily, there are several online tools that can help you determine whether your accounts are secure. Here are a few of the best tools to check whether your online accounts have been hacked or compromised.
Have I Been Pwned
Have I Been Pwned is one of the best ways to check if your online accounts have been compromised. The tool uses your email address to check whether it is associated with any hacked data. Security expert Troy Hunt created the website, which lets users cross-reference their information with databases of breached credentials which were made public on sites like Pastebin.
All you need to do is write your email address in the website’s search bar. The site will then identify whether your email appeared in any compromised data.
If your email address is associated with a data breach, the website specifies the date of the breach, the affected service or company, and details on the leaked data.
You can also use Have I Been Pwned to sign up for a notification service which will let you know if your account appears in any new data breaches.
Facebook Login History
Over time Facebook has released more tools for users to check if their account is secure. The latest such tool lets you check if Facebook sold your data to Cambridge Analytica.
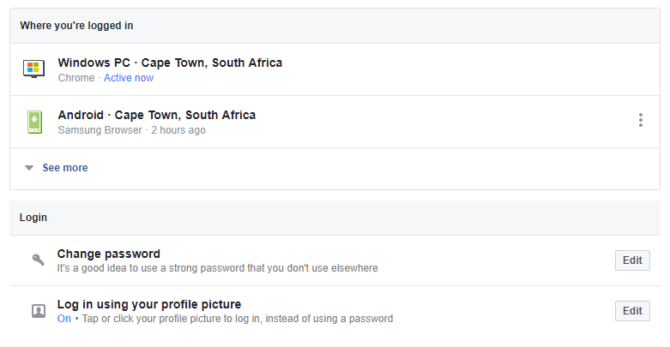
However, your Facebook account dashboard can help you keep tabs on your account security by giving you details on login locations and current active sessions. You can find this tool in under Settings > Security and login.
Facebook provides a list of locations and devices with active sessions under a tab called “Where you’re logged in”. If you see something out of the ordinary, such as an unrecognized device or a location you haven’t visited, you can report it or log out of the session using the drop-down menu next to each listing. The list also lets you see the last login date to give you more context.
If you have tons of active sessions on devices that you’re not using, we recommend you log out of them to increase your overall account security.
BreachAlarm
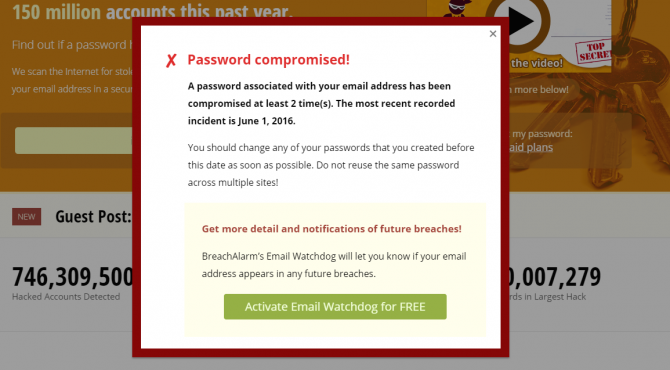
BreachAlarm is an alternative tool to Have I Been Pwned, which uses a similar process to check if an email address is associated with hacked data. It also provides data on leaked passwords.
The main difference between BreachAlarm and Have I Been Pwned is that the former offers a paid service for businesses. This service allows users to subscribe to notifications on data breaches where their email accounts and employee credentials have appeared.
You can also sign up for other plans which offer different levels of email support from BreachAlarm employees.
Sucuri SiteCheck
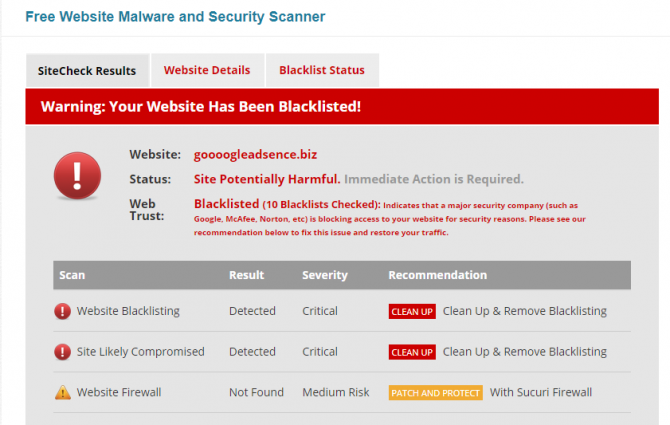
Hackers don’t only target personal online accounts such as social media, but also websites. While bigger websites have a number of security measures in place, websites of small businesses or bloggers often suffer from hacks.
You can check your own website for malware with the Sucuri SiteCheck, a free domain malware scanning tool. Sucuri searches a domain address for any known malware, its blacklisting status, website errors, and any out-of-date software. It will also identify whether you have a website firewall.
We tested the tool with known malware sites versus sites we know are secure to confirm that the tool can accurately identify a compromised site.
While SiteCheck offers users the option to sign up to Sucuri services to address vulnerabilities, the tool is free.
Twitter Account Access History & Permissions
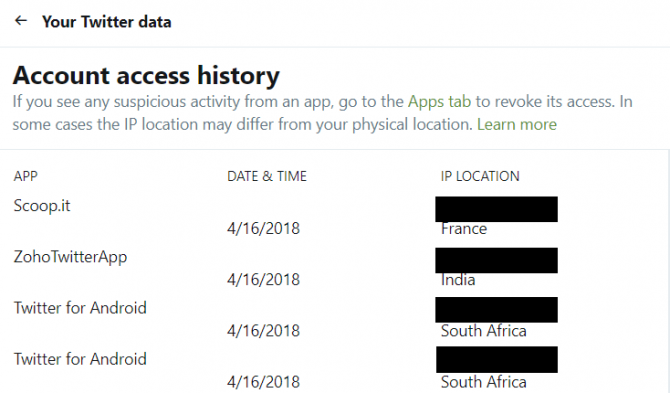
Much like Facebook, Twitter allows users to monitor login locations and active sessions. This can help you determine if an unauthorized third party is accessing your account.
To do this, simply open the Your Twitter Data menu within your Twitter settings. Here you can find a login history for your account. This history includes a list of locations from where your account has been accessed, as well as the app that accessed your account.
If you use scheduling apps such as Zoho Social or Buffer, you can expect to see a few foreign locations in your account history. This is because Twitter is noting the IP Location of the app, rather than the physical location where you are using the app.
Should you see a foreign country in your location history, check under the app names to see whether it’s a service you have authorized. If you see an app you don’t recognize, or one you no longer use, you can revoke access under the Twitter Applications tab.
Pwned Passwords
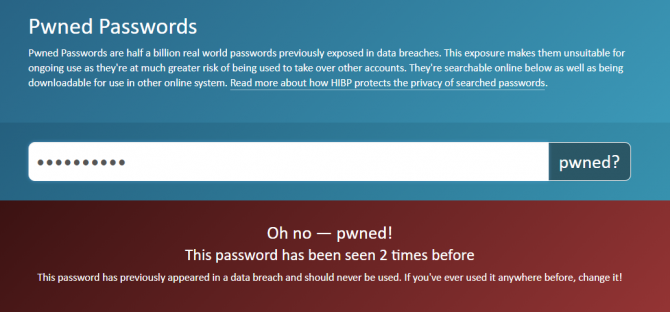
Pwned Passwords is part of Have I Been Pwned, but instead of checking email addresses, the tool checks lists of leaked passwords. This is particularly useful to know as many hackers use credential stuffing to access user accounts.
If you’re a person who recycles their password or uses the same password across all accounts, it’s essential to know whether your password is actually safe. Pwned Passwords includes half a billion passwords exposed by breaches.
The tool does note that even if your password hasn’t appeared in any breaches, this doesn’t mean it is a good password. So even if you get the all-clear, you should make sure to create strong passwords for all your accounts.
Google Accounts: Device Activity and Security Events
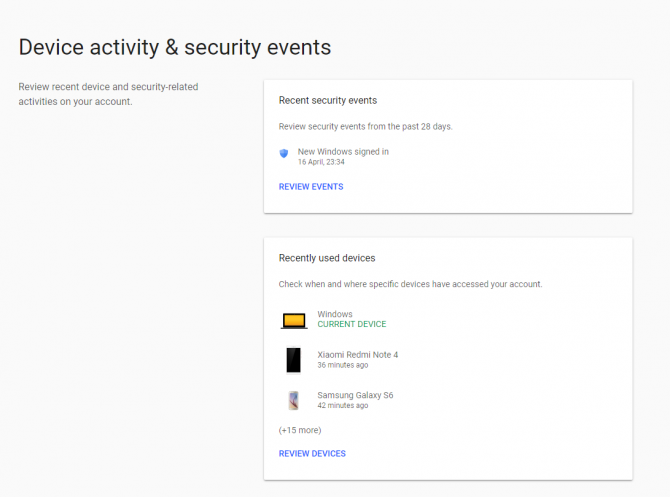
Google’s security tool allows users to check the activity and login locations for all Google-related apps and accounts. In order to access this history, simply sign into your Google profile and select “device activity and security events”. Under this tab, you will see any password changes or added recovery options that have taken place in the past 28 days.
You can also check how many devices are currently logged into your Google accounts. Any security events will also have a geo-location tag, which means that you can check exactly where it happened.
If you notice anything suspicious, you should select the option to Secure Your Account.
To manage the apps which have access to your Google account, go to Sign-in & security > Apps with access to your account > Manage apps. Here you can review your apps and revoke permissions if needed.
Manually Check for Data Breaches
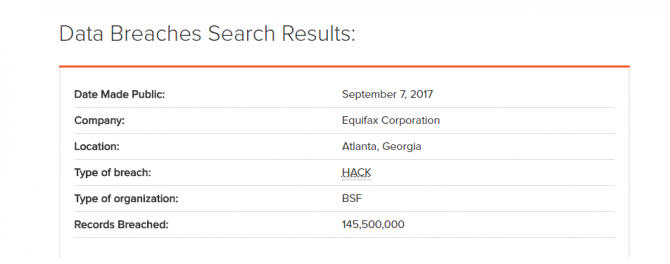
While many of the tools on this list are quite comprehensive, they only allow you to check certain credentials or specific accounts. That’s why using a tool like PrivacyRights.org can be useful to determine your account safety.
The website has a record of all data breaches in the US since 2005. This is a total of over 8,000 breaches.
Privacy Rights acts as a data breach search engine, allowing you to filter results according to company names, industry, date of breaches and more. This requires a bit more effort than the other tools on this list, but it addresses some of the gaps. For example, BreachAlarm and Have I Been Pwned won’t be able to tell you about data breaches of accounts that don’t include your email address—such as online banking accounts or online university accounts.
But with the Privacy Rights search tool, you can check if your bank or university has suffered a data breach in the past decade. Simply search for the name of your institution to see if it was hacked.
The site won’t be able to tell you whether your specific data was compromised. However, by identifying whether an institution was breached, you can get a heads up on whether you should change your login details. For example, searching for Equifax will bring up details about the infamous Equifax data breach.
Don’t Get Hacked While Seeing If You’ve Been Hacked
It incredibly important to keep your accounts secure and to make sure your data isn’t compromised. At the same time, your eagerness to do this should not be the source of a breach.
Some tools available on the web aren’t secure. Or worse, they are posing as security tools but are actually attempting to harvest credentials. This is just one of the ways hackers access your accounts.
When checking up on your account security, make sure to only use tools which others have vouched for. If a third-party site requires you to provide more than a simple email address, rather avoid it.
Even if you haven’t been affected by a breach, you should always consider increasing your online account security. For tips on how to do this, read our guide on setting up two-factor authentication for your social accounts.
Image Credit: belchonock/Depositphotos

