Tight online security has become mandatory for many of us, and, as malicious operators get smarter, tools and protections must get stronger to keep up. Secure Shell (SSH) is an encryption protocol that allows you to send data securely by pairing a public key with a private match.
A variety of situations, including remotely accessing a server or adding security to a Git hosting platform, could require you to generate your own key. Access credentials have become an important part of online security, and macOS and the Terminal app make generating an SSH Key simple. Let’s take a look at the process.
How to Generate an SSH Key Using SSH-Keygen
With the ssh-keygen command you can perform all the functions necessary to generate an SSH key that’s complete and ready to use. During creation, you can specify the algorithm used, length in bits, and other features of your key. For more information on these concepts, refer to later sections of this guide.
The steps for generating an SSH key in macOS are as follows:
Launch Terminal from Applications > Utilities or by doing a Spotlight Search. Enter the ssh-keygen command with the desired parameters.
We’ll discuss variations later, but here’s an example of what a typical ssh-keygen command should look like:
ssh-keygen -t ecdsa -b 521
The desired algorithm follows the -t command, and the required key length comes after the -b input. If you exclude -b, ssh-keygen will use the default number of bits for the key type you’ve selected. A strong encryption algorithm with a good sized key will be most effective at keeping your data safe.
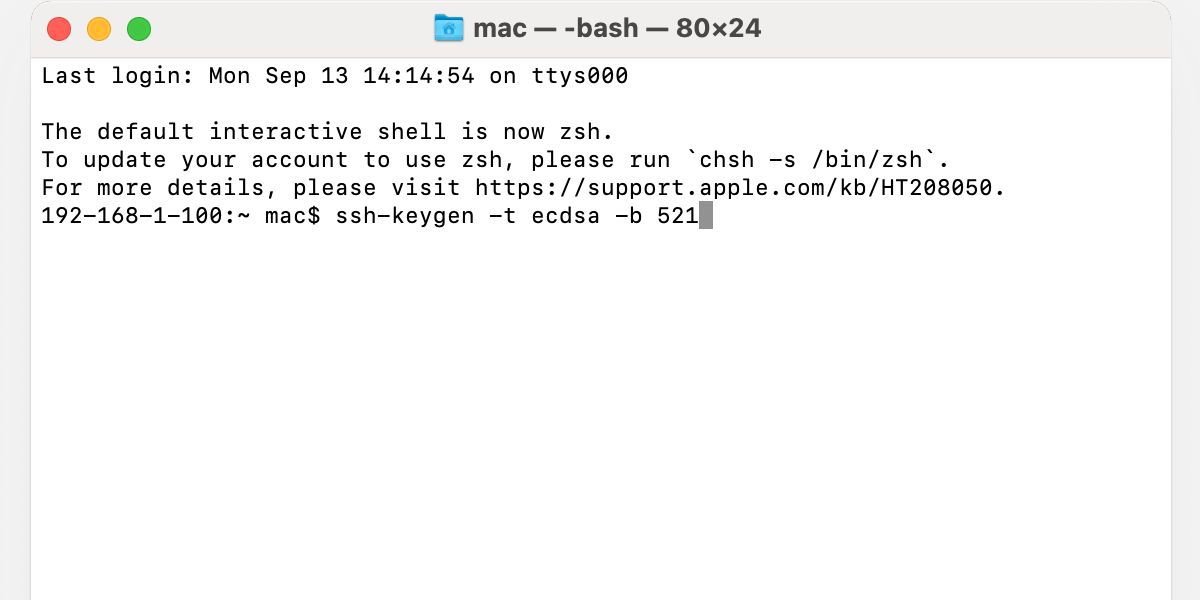
Press Enter to begin the generation progress. Press ENTER again to accept the default file location. You can change this if necessary, but, generally, you’ll want to keep your keys in the suggested folder.
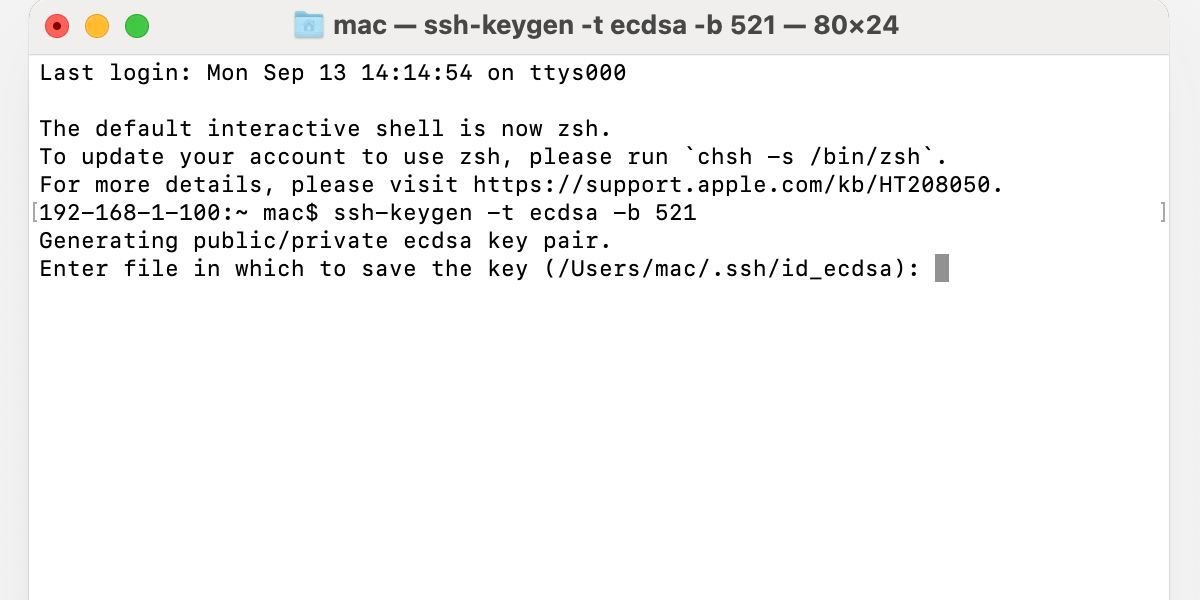
Enter a passphrase when prompted. Although you can leave this blank, we always recommend password-protecting your SSH key. Even if no one else should have access to your device, an extra layer of security is always welcome.
Re-enter your passphrase to complete the process and generate your public and private keys.
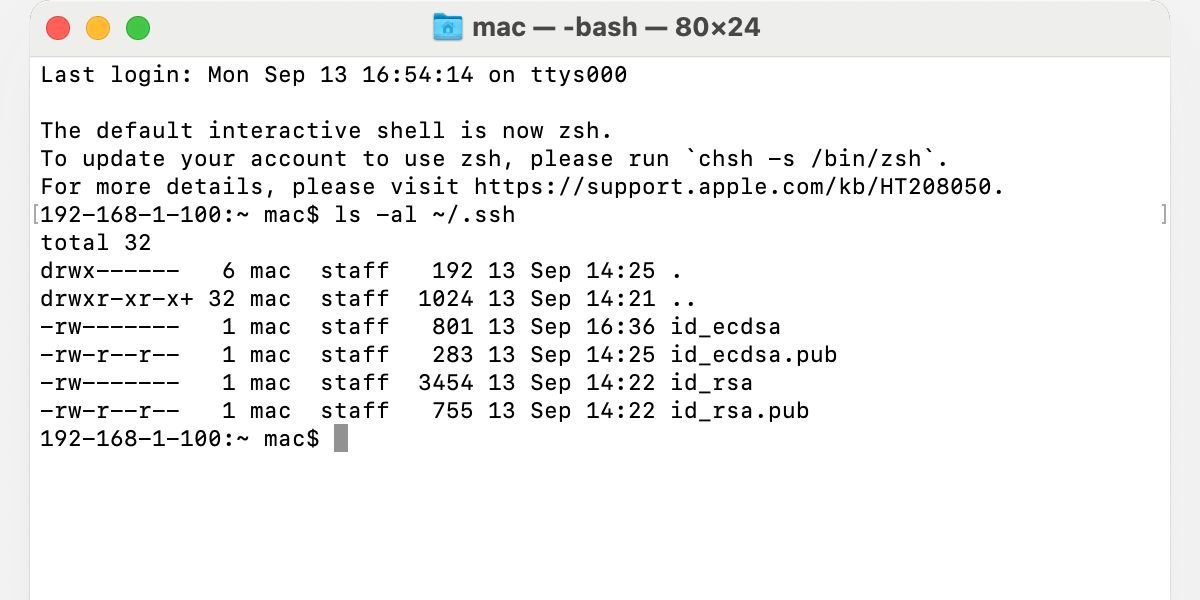
macOS stores both keys in the ~/.ssh/ directory. One file holds your public SSH key, and another contains your private version, which you should never share with anyone.
If Terminal isn’t your thing, several other Mac SSH clients exist, so you can choose the option that best suits your needs.
Copy an SSH Key to Add to Git Hosting Platforms and Other Locations
Once you’ve completed the generation process, you can use Terminal to copy your public key for distribution. You should also note the filename used during creation. In the example provided, macOS stored the public SSH Key in the id_ecdsa.pub file, so that’s the location we’ll need to target.
To copy your public SSH key to the clipboard, follow these steps:
- Launch Terminal.
- Enter the pbcopy < command with the correct file path, for example:
pbcopy < ~/.ssh/id_ecdsa.pub
- Press Enter, and your public key will copy to your clipboard.
From here, you’re free to paste your SSH key to wherever it needs to go. Remember, you should only distribute the public key stored in the .pub file. Your private key is for your use only.
Different SSH Key Types and Sizes
The ssh-keygen command allows you to generate several key types and sizes that use varying algorithms. Firstly, you should confirm which variation your hosting platform, service, or other party recommends before creating your access credentials.
We’ll list the most common SSH key types here and explain the characteristics of each one:
- RSA: A widely supported algorithm, RSA is a strong choice for many situations. Length is strength, and you’ll want to create a key of 2048 or 4096 bits, with the former being sufficient and the latter being ideal.
- ECDSA: A newer algorithm, ECDSA provides a similar level of security to RSA but with shorter keys, translating to quicker performance. Supported key sizes are 256, 384, and 521 bits.
- Ed25519: An emerging algorithm, Ed25519 improves on the security and performance of previous key types. Apple itself uses this authentication method in some instances, including during communication between certain devices. Keys are only 256 bits long while still providing high level security.
When generating your SSH key, ensure that you enter the desired algorithm type following the -t command.
Useful Commands to Know When Creating an SSH Key on Mac
We’ve discussed the basic components of the ssh-keygen command; however, in some cases, you may wish to perform other functions. Here, we’ll list some relevant commands and their uses:
- -t: Use this command to input the algorithm you wish to use. RSA, ECDSA, and Ed25519 are common and viable choices.
- -b: Specify your key length by inputting the number of bits used. Before entering the -b command, always check the requirements of the chosen algorithm, as some restrictions apply.
- -p: You can change your key’s passphrase with the -p command. Simply include -p with ssh-keygen, and Terminal will request the file location. Enter the path of the relevant key and create a new passphrase when prompted.
- -f: Use the -f command to direct ssh-keygen to a specific file location.
- -C: The -C command adds a comment to your key, which is a useful labeling method.
Additionally, the ls command will list all the SSH keys stored in the default directory:
ls -al ~/.ssh
To remove a local SSH key, you can use the rm command in terminal, for example:
rm ~/.ssh/id_ecdsa
and
rm ~/.ssh/id_ecdsa.pub
Finally, to access a complete list of commands, the following input will display all available options along with additional information:
man ssh-keygen
macOS Makes SSH Key Generation Easy
Generating an SSH key is simple in macOS. Terminal and the ssh-keygen tool can perform all the necessary functions to design, create, and distribute your access credentials, so there’s no need for additional software. Simply input the correct commands and ssh-keygen does the rest.
Common algorithms used are RSA, ECDSA, and Ed25519, and each type has its own specifications and usable key lengths. During creation, you can specify these details and input other instructions using the right commands. Afterwards, you can continue to use Terminal to copy, modify, and delete your stored keys.
Whether for fun or function, knowing how to generate your own access credentials is a valuable skill to learn. As our lives move further online, securing our private data is important, and the wise will use every tool at their disposal.